-
Compteur de contenus
4 684 -
Inscription
-
Dernière visite
Type de contenu
Profils
Forums
Blogs
Messages posté(e)s par eikichi
-
-
Si preneur du lot un waterblock HK 3.0 LT et un rad 360 phobya en cadeau .
séparé :
980x : 750€in
Classifield + block ek : 165€in
en lot :
I7 980x 3031a261 , bench à 5.1ghz version box , facture / Classifield e760 avec waterblock EK , facture / 3*2Go Dominator GT pc 14900 C7
prix : 1050€ in
ou possibilité d'échange contre M4E /2600K / Gskills Ripjaws x + roros de vôtre part .
screen :
-
Salut,
au cas ou je vends une 470 sc evga : http://forum.zebulon.fr/vdsevga-470-sc-neuve-160-t182247.html
-
Bonsoir, donc je vends une evga 470 sc toute neuve sous blister garantie 10ans , facture, bundle prix 160€
-
le i7 920 n'est pas un processeur qui excelle en overclocking .
Ce qu'il faut pas lire mais n'importe quoi ce que tu dis arrète de donner des conseils si c'est pour sortir des inepties de la sorte !
-
Salut, la TJ est de 100° sur les Q9XXX et de 95° sur les QX9650 et 85° sur les QX9770 .
http://www.tomshardware.co.uk/intel-dts-sp...news-29460.html
-
Bonsoir et merci DAVY mais si tu peux expliquer j'ai des possibilités très limitées avec mon bios
Sur une DFI , tu es limité niveau fonction du bios cela m'étonne sachant que les DFI ont les bios les plus détaillés que les autres cm.
-
Salut, je possède cette cm donc quel problème as tu ? sinon colle ici déjà tes réglages genre:
Cpu ratio:
blck:
dram frequ:
ulck:
Qpi Frequ:
timmings ram:
vcpu:
vioh:
cpu pll:
qpi dram:
llc:
Sinon ici http://www.overclocking-pc.fr/forums/ y a pas mal de monde ayant cette cm si cela peut aider .
-
-
oui tout les symptômes ont disparu , encore merci pour ton aide
 .
. -
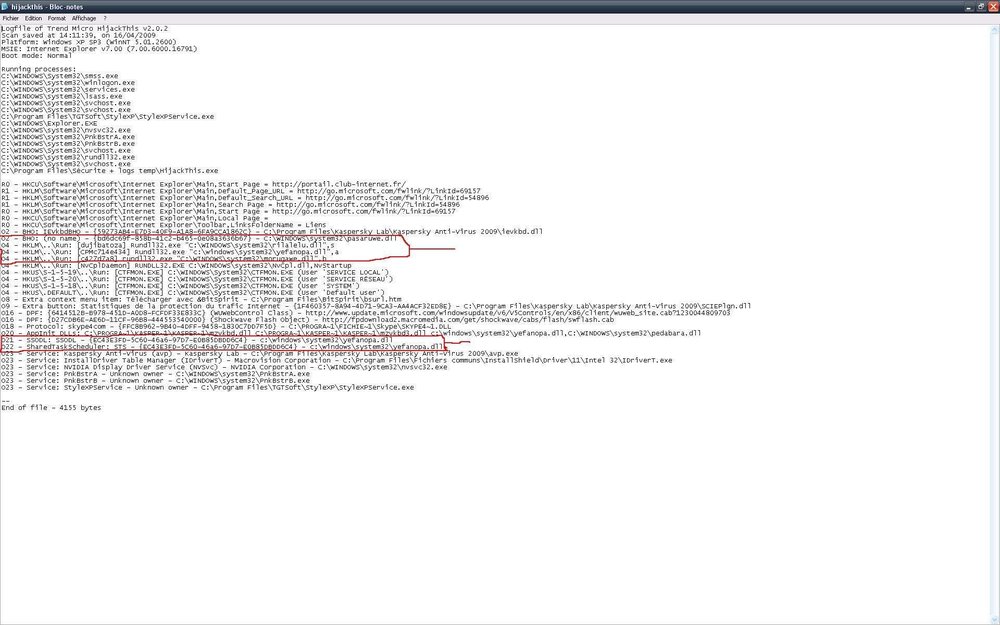
voici hijackthis :
Logfile of Trend Micro HijackThis v2.0.2
Scan saved at 17:06:22, on 16/04/2009
Platform: Windows XP SP3 (WinNT 5.01.2600)
MSIE: Internet Explorer v7.00 (7.00.6000.16791)
Boot mode: Normal
Running processes:
C:\WINDOWS\System32\smss.exe
C:\WINDOWS\system32\winlogon.exe
C:\WINDOWS\system32\services.exe
C:\WINDOWS\system32\lsass.exe
C:\WINDOWS\system32\svchost.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\Explorer.EXE
C:\WINDOWS\system32\nvsvc32.exe
C:\WINDOWS\system32\PnkBstrA.exe
C:\WINDOWS\system32\PnkBstrB.exe
C:\WINDOWS\System32\svchost.exe
C:\WINDOWS\system32\RunDLL32.exe
C:\WINDOWS\System32\svchost.exe
C:\program files\valve\steam\steam.exe
C:\WINDOWS\system32\ctfmon.exe
C:\Program Files\Sécurite + logs temp\sanner.exe
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Start Page = http://portail.club-internet.fr/
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Page_URL = http://go.microsoft.com/fwlink/?LinkId=69157
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Default_Search_URL = http://go.microsoft.com/fwlink/?LinkId=54896
R1 - HKLM\Software\Microsoft\Internet Explorer\Main,Search Page = http://go.microsoft.com/fwlink/?LinkId=54896
R0 - HKLM\Software\Microsoft\Internet Explorer\Main,Start Page = http://go.microsoft.com/fwlink/?LinkId=69157
R0 - HKCU\Software\Microsoft\Internet Explorer\Main,Local Page =
R0 - HKCU\Software\Microsoft\Internet Explorer\Toolbar,LinksFolderName = Liens
O2 - BHO: IEVkbdBHO - {59273AB4-E7D3-40F9-A1A8-6FA9CCA1862C} - C:\Program Files\Kaspersky Lab\Kaspersky Anti-Virus 2009\ievkbd.dll
O4 - HKLM\..\Run: [NvMediaCenter] RunDLL32.exe NvMCTray.dll,NvTaskbarInit
O4 - HKLM\..\Run: [NvCplDaemon] RUNDLL32.EXE C:\WINDOWS\system32\NvCpl.dll,NvStartup
O4 - HKCU\..\Run: [sTYLEXP] C:\Program Files\TGTSoft\StyleXP\StyleXP.exe -Hide
O4 - HKCU\..\Run: [steam] "c:\program files\valve\steam\steam.exe" -silent
O4 - HKCU\..\Run: [CTFMON.EXE] C:\WINDOWS\system32\ctfmon.exe
O4 - HKUS\S-1-5-19\..\Run: [CTFMON.EXE] C:\WINDOWS\System32\CTFMON.EXE (User 'SERVICE LOCAL')
O4 - HKUS\S-1-5-20\..\Run: [CTFMON.EXE] C:\WINDOWS\System32\CTFMON.EXE (User 'SERVICE RÉSEAU')
O4 - HKUS\S-1-5-18\..\Run: [CTFMON.EXE] C:\WINDOWS\System32\CTFMON.EXE (User 'SYSTEM')
O4 - HKUS\.DEFAULT\..\Run: [CTFMON.EXE] C:\WINDOWS\System32\CTFMON.EXE (User 'Default user')
O8 - Extra context menu item: Télécharger avec &BitSpirit - C:\Program Files\BitSpirit\bsurl.htm
O9 - Extra button: Statistiques de la protection du trafic Internet - {1F460357-8A94-4D71-9CA3-AA4ACF32ED8E} - C:\Program Files\Kaspersky Lab\Kaspersky Anti-Virus 2009\SCIEPlgn.dll
O16 - DPF: {6414512B-B978-451D-A0D8-FCFDF33E833C} (WUWebControl Class) - http://www.update.microsoft.com/windowsupd...b?1230044809703
O16 - DPF: {D27CDB6E-AE6D-11CF-96B8-444553540000} (Shockwave Flash Object) - http://fpdownload2.macromedia.com/get/shoc...ash/swflash.cab
O18 - Protocol: skype4com - {FFC8B962-9B40-4DFF-9458-1830C7DD7F5D} - C:\PROGRA~1\FICHIE~1\Skype\SKYPE4~1.DLL
O20 - AppInit_DLLs: C:\PROGRA~1\KASPER~1\KASPER~1\mzvkbd.dll C:\PROGRA~1\KASPER~1\KASPER~1\mzvkbd3.dll ,
O23 - Service: Kaspersky Anti-Virus (avp) - Kaspersky Lab - C:\Program Files\Kaspersky Lab\Kaspersky Anti-Virus 2009\avp.exe
O23 - Service: InstallDriver Table Manager (IDriverT) - Macrovision Corporation - C:\Program Files\Fichiers communs\InstallShield\Driver\11\Intel 32\IDriverT.exe
O23 - Service: NVIDIA Display Driver Service (NVSvc) - NVIDIA Corporation - C:\WINDOWS\system32\nvsvc32.exe
O23 - Service: PnkBstrA - Unknown owner - C:\WINDOWS\system32\PnkBstrA.exe
O23 - Service: PnkBstrB - Unknown owner - C:\WINDOWS\system32\PnkBstrB.exe
O23 - Service: StyleXPService - Unknown owner - C:\Program Files\TGTSoft\StyleXP\StyleXPService.exe
--
End of file - 3855 bytes
sinon est ce que je peux supprimer tout ce qui est en quarantaine sur mbam ?
-
alors voici le rapport :
Malwarebytes' Anti-Malware 1.36
Version de la base de données: 1989
Windows 5.1.2600 Service Pack 3
16/04/2009 16:55:28
mbam-log-2009-04-16 (16-55-28).txt
Type de recherche: Examen complet (C:\|E:\|)
Eléments examinés: 222288
Temps écoulé: 59 minute(s), 2 second(s)
Processus mémoire infecté(s): 0
Module(s) mémoire infecté(s): 5
Clé(s) du Registre infectée(s): 19
Valeur(s) du Registre infectée(s): 8
Elément(s) de données du Registre infecté(s): 4
Dossier(s) infecté(s): 0
Fichier(s) infecté(s): 15
Processus mémoire infecté(s):
(Aucun élément nuisible détecté)
Module(s) mémoire infecté(s):
c:\WINDOWS\system32\yefanopa.dll (Trojan.Vundo.H) -> Delete on reboot.
C:\WINDOWS\system32\pedabara.dll (Trojan.Vundo.H) -> Delete on reboot.
C:\WINDOWS\system32\pasaruwe.dll (Trojan.Vundo.H) -> Delete on reboot.
C:\WINDOWS\system32\rilalelu.dll (Trojan.Vundo.H) -> Delete on reboot.
C:\WINDOWS\system32\morugawe.dll (Trojan.Vundo.H) -> Delete on reboot.
Clé(s) du Registre infectée(s):
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Browser Helper Objects\{bd6dc69f-858b-41c2-b465-0e08a3636b67} (Trojan.Vundo.H) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{bd6dc69f-858b-41c2-b465-0e08a3636b67} (Trojan.Vundo.H) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\CLSID\{ec43e3fd-5c60-46a6-97d7-e0b85dbdd6c4} (Trojan.Vundo.H) -> Delete on reboot.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{bd6dc69f-858b-41c2-b465-0e08a3636b67} (Trojan.Vundo.H) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\Typelib\{9233c3c0-1472-4091-a505-5580a23bb4ac} (Trojan.FakeAlert) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{02715e47-5a8e-495b-8f63-0d30470b8e72} (Trojan.Vundo) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{a8eeb996-62aa-4e48-995d-eaddcac47476} (Trojan.Vundo) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{1a26f07f-0d60-4835-91cf-1e1766a0ec56} (Trojan.Agent) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{1a93c934-025b-4c3a-b38e-9654a7003239} (Adware.Gamesbar) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Ext\Stats\{6f282b65-56bf-4bd1-a8b2-a4449a05863d} (Adware.Gamesbar) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Mozilla\MSFox (Trojan.Agent) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\contim (Trojan.Vundo) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\dslcnnct (Trojan.Vundo) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\IProxyProvider (Trojan.Vundo) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\rdfa (Trojan.Vundo) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\RemoveRP (Trojan.Vundo) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\LPVideoPlugin (Trojan.FakeAlert) -> Quarantined and deleted successfully.
HKEY_CLASSES_ROOT\AppID\LPVideo.DLL (Trojan.FakeAlert) -> Quarantined and deleted successfully.
HKEY_CURRENT_USER\SOFTWARE\XML (Trojan.FakeAlert) -> Quarantined and deleted successfully.
Valeur(s) du Registre infectée(s):
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\c427d7a8 (Trojan.Vundo.H) -> Delete on reboot.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\cpmc714e434 (Trojan.Vundo.H) -> Delete on reboot.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\dujibatoza (Trojan.Vundo.H) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\gzpinit_dlls (Spyware.Agent.H) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SharedTaskScheduler\{ec43e3fd-5c60-46a6-97d7-e0b85dbdd6c4} (Trojan.Vundo.H) -> Delete on reboot.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\ShellServiceObjectDelayLoad\ssodl (Trojan.Vundo.H) -> Delete on reboot.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ShellExecuteHooks\{02715e47-5a8e-495b-8f63-0d30470b8e72} (Trojan.Vundo) -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\ShellExecuteHooks\{a8eeb996-62aa-4e48-995d-eaddcac47476} (Trojan.Vundo) -> Quarantined and deleted successfully.
Elément(s) de données du Registre infecté(s):
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\AppInit_DLLs (Trojan.Vundo.H) -> Data: c:\windows\system32\yefanopa.dll -> Delete on reboot.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Windows\AppInit_DLLs (Trojan.Vundo.H) -> Data: c:\windows\system32\pedabara.dll -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA\Notification Packages (Trojan.Vundo.H) -> Data: c:\windows\system32\pedabara.dll -> Quarantined and deleted successfully.
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center\UpdatesDisableNotify (Disabled.SecurityCenter) -> Bad: (1) Good: (0) -> Quarantined and deleted successfully.
Dossier(s) infecté(s):
(Aucun élément nuisible détecté)
Fichier(s) infecté(s):
C:\WINDOWS\system32\morugawe.dll (Trojan.Vundo.H) -> Delete on reboot.
C:\WINDOWS\system32\ewagurom.ini (Trojan.Vundo.H) -> Quarantined and deleted successfully.
c:\WINDOWS\system32\yefanopa.dll (Trojan.Vundo.H) -> Delete on reboot.
C:\WINDOWS\system32\rilalelu.dll (Trojan.Vundo.H) -> Delete on reboot.
C:\WINDOWS\system32\pasaruwe.dll (Trojan.Vundo.H) -> Delete on reboot.
C:\WINDOWS\system32\pedabara.dll (Trojan.Vundo.H) -> Delete on reboot.
C:\Program Files\Sécurite + logs temp\backups\backup-20090416-133014-573.dll (Trojan.Vundo.H) -> Quarantined and deleted successfully.
C:\Program Files\Sécurite + logs temp\backups\backup-20090416-135458-307.dll (Trojan.Vundo.H) -> Quarantined and deleted successfully.
C:\Program Files\Sécurite + logs temp\backups\backup-20090416-135613-746.dll (Trojan.Vundo.H) -> Quarantined and deleted successfully.
C:\Program Files\Sécurite + logs temp\backups\backup-20090416-141156-866.dll (Trojan.Vundo.H) -> Quarantined and deleted successfully.
C:\Program Files\Sécurite + logs temp\backups\backup-20090416-153511-404.dll (Trojan.Vundo.H) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\leheziti.dll (Trojan.Vundo.H) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\mcrh.tmp (Malware.Trace) -> Quarantined and deleted successfully.
C:\WINDOWS\pskt.ini (Trojan.Vundo) -> Quarantined and deleted successfully.
C:\WINDOWS\system32\clkcnt.txt (Trojan.Vundo) -> Quarantined and deleted successfully.
-
Salut, donc je me trouve face à un soucis de virus après plusieurs scan de kaspersky qui lui ne les détectent pas et avec hijackthis impossible de les fixer , ils se lancent toujours au démarrage et maintenant en pleins jeux j'ai des retour sur le bureau du à cela .
voici le screen de hijackthis ils sont entourés en rouge :
os officiel pour les sceptiques, av kaspersky 2009 .
merci de vôtre aide ...
-
200in le lot cm et ram .
-
nouveau prix pour le lot cm+ram 220€ fdpin jusqu' a demain matin .
-
Salut, pourquoi ne pas acheter tes pièces toi même ? sinon le pc du lien est pas mal .
-
-
-
Baisse de prix de la cm à 130€ , la ram 125€ et l'alim 160€ .
les prix sont avec les fdpin .
-
Salut, tu comptes overclocker ton pc ? si oui dans ce cas là un bon ventirad sera pas négligeable sachant que les i7 chauffent pas mal après augmentation du vcore ensuite la ram Gskill nq sera bien pour tourner d'origine mais sinon regarde plutôt pour la gskill pi black en pc 12800 qui sont de meilleurs facture.
-
-
à vendre :
p5e3 ws pro (s775) qui date du mois d'aout 2008 , toujours garantie , facture , bundle complet .
prix demandé 120€
Mémoire Gskill HZ pc 12800 équipé de puces GTS , encore garantie , boite, facture .
Précision ces Gskills tiennent 2200mhz en benchs screens sur jmax-oc (ancien proprio antoine-76) sinon tiennent les 2000mhz en 7/7/7/18 1T à 2.06v , tourne en ce moment en 7/6/5/15 1T à 1600mhz entre 1.86v à 1.9v .
Les 1800mhz en cas 7 à 2.0v donc d'excellente ram et ne pas oublier que les puces GTS sont très rare maintenant .
prix demandé : 120€
Tout le matos est en excellent état livré dans les boites d'origine et bien entendu facture et l'envoi sera en colisimo suivi avec assurance
-
dsl vendu et un qx9770 est identique au qx9650 mis à part qu'il tourne à 3.2ghz et à un tdp de 150w donc pas trop d'intérêt .
-
Salut, donc je vends un qx9650 L741b156 version box datant de juillet 2008 , facture et cgnie .
Tourne à 4.0ghz pour 1.36v , ne chauffe pas car il est sous un hr01 plus + scythe kama 1000rpm .
raison de la vente je dispose d'un 2ème QX donc plus l'utilité de celui-ci.
prix demandé : 350€
-









[vds]980x/ classifield 760/ dominator GT pc 14900
dans Conseils matériel - Achats & Ventes
Posté(e)
prix négociable .